Multi-factor authentication also known as MFA is one of the most popular ways of securely authenticating users. Needless to say it forms one of the main core component of identity and access management of any application architecture.
While MFA is generally used for account logins we can also use MFA to protect data from accidental deletion. Today in this blog article we will cover the feature of MFA delete available for AWS S3 buckets.
MFA delete: Simply putting it MFA delete protects the versioning of the file in S3 bucket. This means that when a file in S3 bucket is deleted, the version of the file is preserved even though the file is deleted from the bucket.
Prerequisites:
AWS account - Since the MFA delete feature will be demonstrated on S3 in AWS
MFA enabled in the root account - This can be verified by navigating to Account --> My Security credentials --> Multi-factor authentication (MFA)
AWS guide has steps for setting for virtual MFA device.
Serial Number of MFA device: Note down the serial number of the MFA device from the MFA table displayed in the Security Credentials tab. This will be used later.
AWS CLI : Currently MFA Delete option can only be enabled and disabled using AWS CLI/AWS SDK and Amazon S3 REST API. We will be using AWS CLI. It can be downloaded and installed from AWS site here
Generate a set of access key ID and secret access key for you root MFA account. Steps for generating them are listed on AWS guide here. This will be used late while working with AWS CLI.
Please note that the best practice is to never create a access key for your root account. Never ever share or post the access keys for root account online.
We remove the access keys after the MFA-delete demo.
Steps:
1. Creating a S3 bucket
(This step can be skipped in you already have S3 bucket)
- Click "Create bucket" option from S3 service in AWS
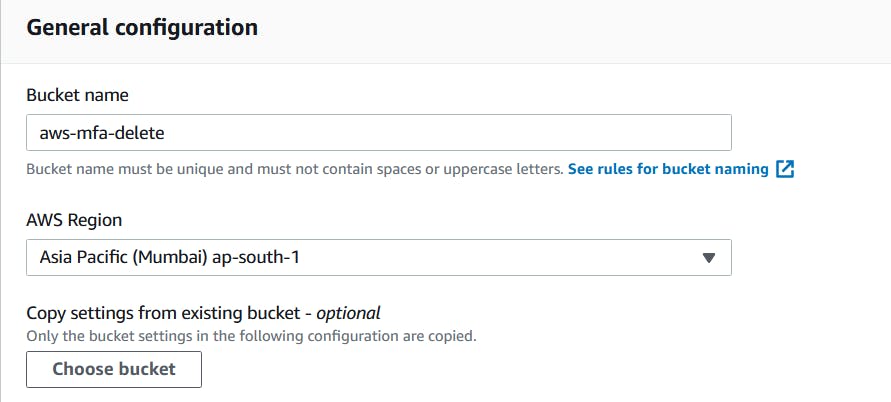
- Give some dummy name for your bucket. In my case the name is "aws-mfa-delete"
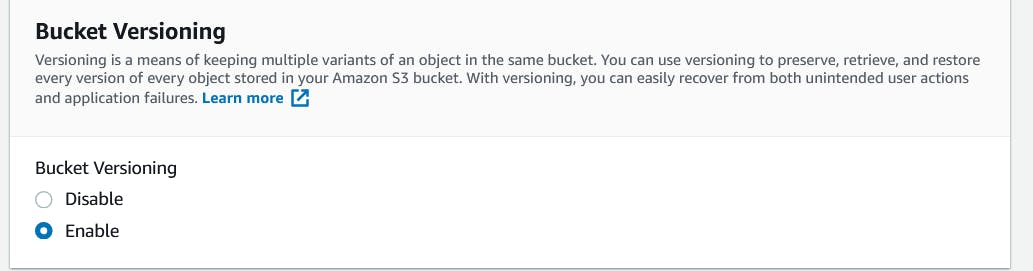
- Make sure to scroll down and enable bucket versioning
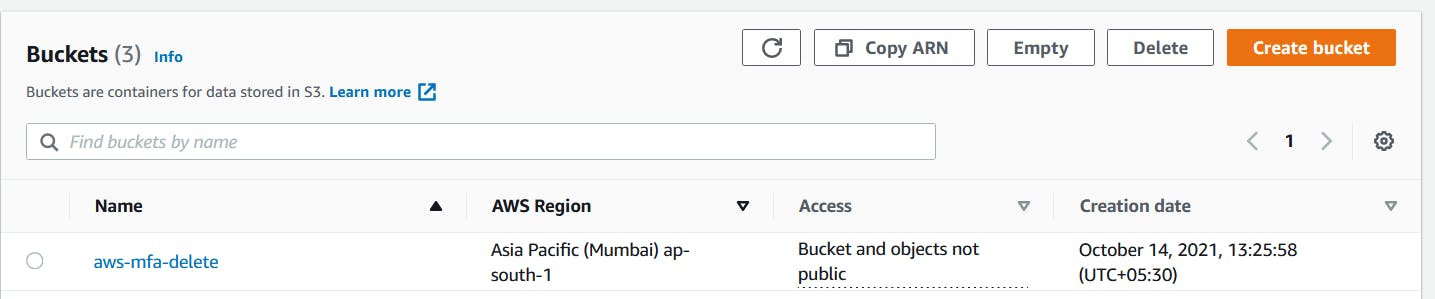
Scroll down and hit "Create bucket" to create the S3 bucket.
The bucket should now be visible in the list of available buckets.
- Click on the newly created bucket and navigate to Properties tab and scroll down to Bucket Versioning part. You should see MFA delete status as disabled.
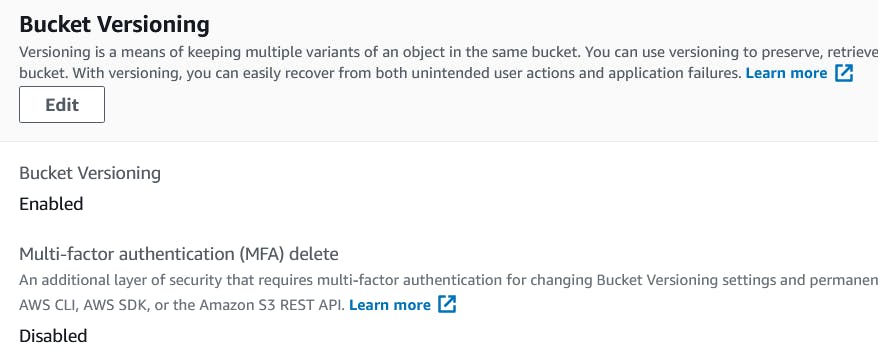
2. Enabling MFA Delete
- Open the cmd terminal to start working with AWS CLI. As stated earlier MFA delete feature can be enabled or disabled using AWS CLI.
- Setup a profile using the following command. Profile name can be of your choice. Here I have named it as "mfa-delete-demo"
aws configure --profile mfa-delete-demo
On pressing enter it will ask for Access key id and Secret Key. Provide them as generated in prerequisites step number 5. Provide the default region name and default output format. The last two can be left blank.
After the authentication is done run the following command to find the list of S3 buckets. You should see the newly created S3 bucket listed which we created earlier.
aws s3 ls --profile mfa-delete-demo
- Once the bucket listed correctly type in the below command.
aws s3api put-bucket-versioning --bucket aws-mfa-delete --versioning-configuration Status=Enabled,MFADelete=Enabled --mfa "**your mfa-device-arn** **mfa-code**" --profile mfa-delete-demo
Make sure:
- To replace the text "your-mfa-device-arn" with the device serial noted in Prerequisites step number three.
- To replace the text "mfa-code" with the MFA code generated on your device
In case using different bucket or profile be sure to change the above command to the one needed
Once the above command executes without any error go back to AWS console to check the MFA status. The status should be updated to show MFA Delete as enabled
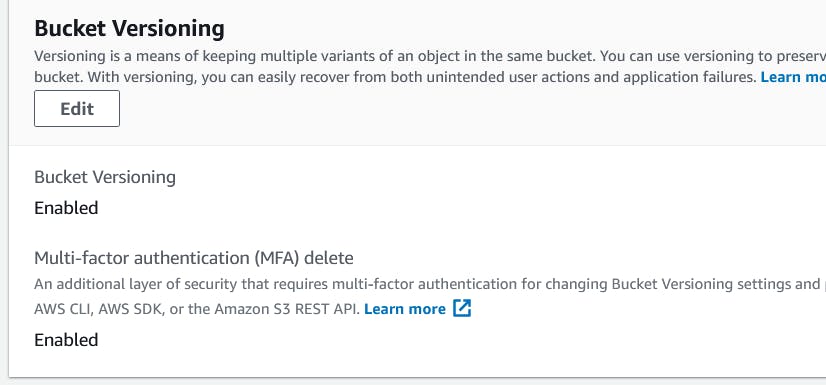
Congratulations!! 🥳🥳 MFA Delete feature has been successfully implemented on S3 bucket 😎
3. Testing MFA Delete
- Now try to delete an object in the bucket
- You should be able to delete the object. Since versioning is enabled AWS will put a delete marker and retain all the versions of the file
- Toggle the "Show versions" button to find the versions
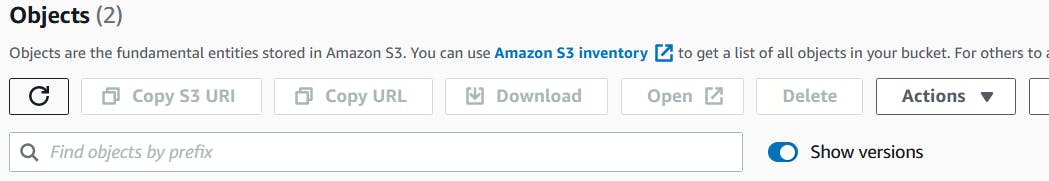
Select the version and try to delete the object
You will get an error stating MFA delete is enabled.
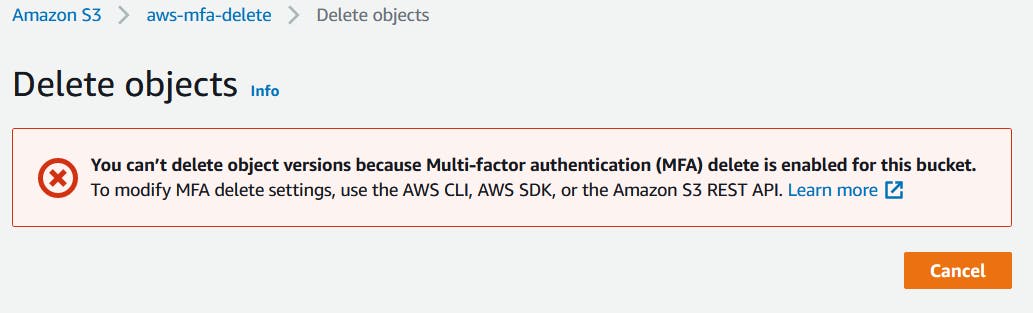
4. Disabling MFA Delete
- To disable the MFA Delete feature for a bucket go back to AWS CLI and run the following command
aws s3api put-bucket-versioning --bucket aws-mfa-delete --versioning-configuration Status=Enabled,MFADelete=Disabled --mfa "**your mfa-device-arn** **mfa-code**" --profile mfa-delete-demo
Once again make sure of the following :
- To replace the text "your-mfa-device-arn" with the device serial noted in Prerequisites step number three.
- To replace the text "mfa-code" with the MFA code generated on your device
- In case using different bucket or profile be sure to change the above command to the one needed
Once the above command executes without any error go back to AWS console to check the MFA status. The status should now show MFA Delete as disabled
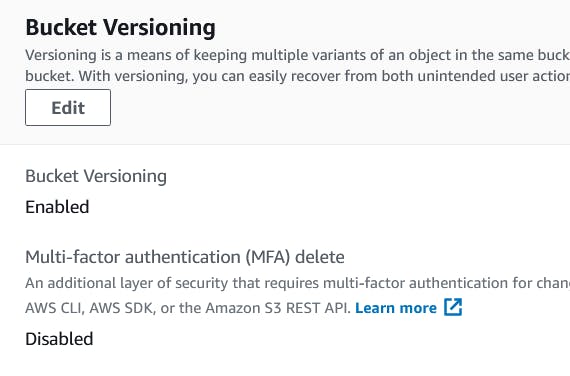
And now version of objects in the bucket can be deleted from console without any errors. Alternatively the objects in a bucket can be deleted without removing MFA delete on the bucket. For this the following command can be used -
aws s3api delete-object --bucket **bucket-name** --key **object name** --version-id **Object version id** --profile **aws-named-profile** --mfa "**your mfa-device-arn** **mfa-code**"
Make sure to replace the "** **" part with details of the bucket on which the command has to be run
5. Delete the Root access keys
- Navigate to My Security credentials from top right of the AWS console
- Go to Access keys tab
- Make sure to deactivate you access key for root account. If not going to be used in future it is advisable to delete them permanently. Best practice is to create IAM user with least privilege and generate access keys under this IAM user.
Conclusion
In this blog article we implemented a method to secure the files stored on S3 bucket using versioning and MFA delete features offered by AWS. MFA delete can only be enabled and disabled by root account thereby adds an extra layer of security.
Thanks for reading this blog article 😃
Until next time : Happy Learning 📖
